Protecting Your Digital Assets with Expert Cybersecurity Solutions
ADAS Technologies is a leading cybersecurity services provider with a team of trained and expert cybersecurity enthusiasts dedicated to protecting organizations from evolving cyber threats.

Why Choose ADAS Technologies?
Advanced Threat Protection
Stay ahead of emerging cyber threats with our cutting-edge security solutions and threat intelligence.
Expert Team
Our certified cybersecurity professionals bring years of experience in threat detection and incident response.
Comprehensive Analysis
From penetration testing to malware analysis, we provide complete security assessments.
24/7 Support
Round-the-clock monitoring and support to ensure your systems remain secure at all times.
Network Security & Information Protection

Comprehensive Network Security
Multi-layered protection including firewalls, intrusion prevention systems, network access control, antivirus sandboxing, remote access VPNs, and web filtering to secure your infrastructure.
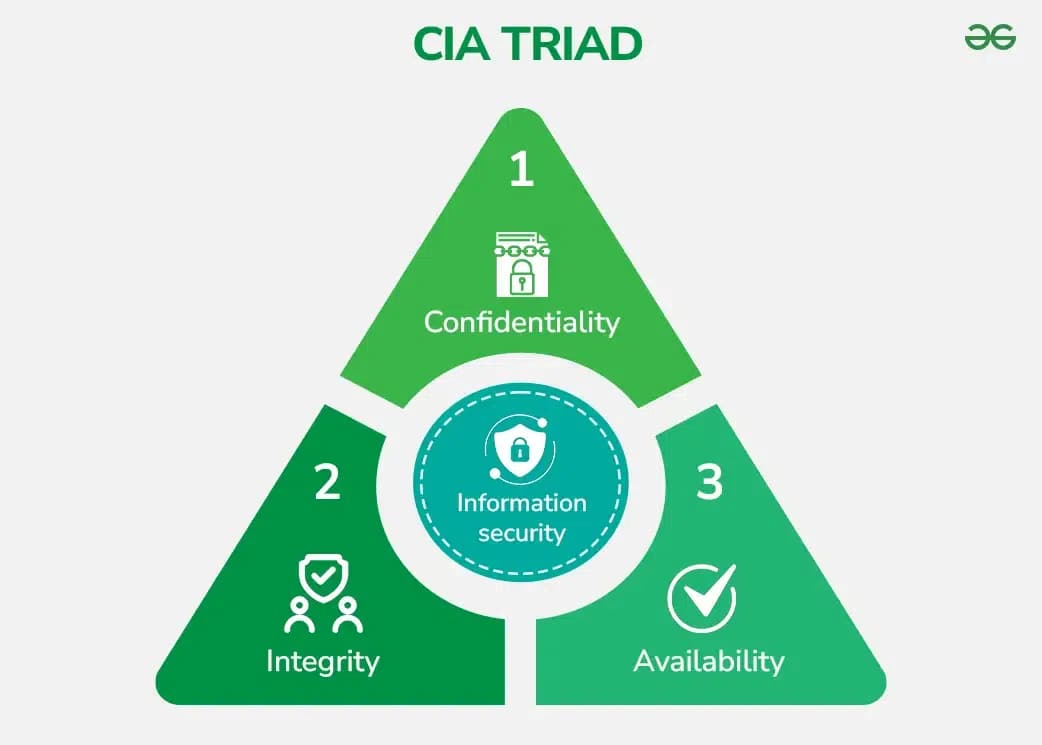
Information Security Fundamentals
Our security approach is built on the CIA Triad principles: ensuring Confidentiality, Integrity, and Availability of your critical information assets through comprehensive security measures.
About ADAS Technologies
ADAS Technologies is a leading cybersecurity services provider with a team of trained and expert cybersecurity enthusiasts dedicated to protecting organizations from evolving cyber threats.
Our Mission
To protect organizations' digital assets through cutting-edge security solutions, enabling them to operate securely in the digital age while maintaining business continuity and trust.
Our Vision
To be the leading cybersecurity services provider, setting industry standards for excellence, innovation, and trust in digital security solutions.
Our Values
Excellence
Delivering outstanding results through continuous improvement and dedication to quality in every security solution we provide.
Innovation
Embracing cutting-edge technologies and methodologies to stay ahead of evolving cyber threats and provide advanced security solutions.
Trust
Building long-term partnerships based on reliability, confidentiality, and proven expertise in cybersecurity services.
Expertise
Maintaining the highest levels of professional knowledge and skills through continuous learning and industry certifications.
Our Expert Team
Our team consists of certified cybersecurity professionals with extensive experience in threat assessment, vulnerability management, and security architecture. We continuously update our skills to stay ahead of the evolving threat landscape.
Our Cybersecurity Services
Comprehensive security solutions to protect your organization from cyber threats
Penetration Testing
Comprehensive security assessments to identify vulnerabilities in your systems and networks before malicious actors can exploit them.
Red Team Assessments
Advanced threat simulation exercises that test your organization's detection and response capabilities through realistic attack scenarios.
Source Code Analysis
Static code security analysis to identify security vulnerabilities and ensure secure coding practices in your applications.
SAST & DAST
Static and Dynamic Application Security Testing solutions to identify vulnerabilities throughout the software development lifecycle.
Malware Analysis
Advanced threat analysis and reverse engineering services to understand and mitigate sophisticated malware threats.
Red Team vs Blue Team Security Approach

We provide both offensive (Red Team) and defensive (Blue Team) security services to give you comprehensive protection and testing capabilities. Our Red Team conducts ethical hacking and penetration testing, while our Blue Team focuses on threat hunting, incident response, and infrastructure protection.
🔍 Penetration Testing
Comprehensive security assessments to identify vulnerabilities in your systems and networks before malicious actors can exploit them.
What is Penetration Testing?
Our penetration testing services provide thorough security assessments using industry-standard methodologies. We simulate real-world attacks to identify vulnerabilities, assess security controls, and provide detailed remediation recommendations.
Key Benefits
- Early vulnerability detection before attackers can exploit them
- Comprehensive assessment of security controls and defenses
- Real-world attack simulation using advanced techniques
- Detailed reporting with actionable remediation guidance
- Compliance with industry security standards and regulations
Types of Penetration Testing
Web Application Testing
Comprehensive testing of web applications for OWASP Top 10 vulnerabilities and advanced security flaws
Network Penetration Testing
Assessment of network infrastructure, firewalls, and internal security controls
Wireless Security Testing
Evaluation of wireless network security, encryption, and access controls
Cloud Security Testing
Security assessment of cloud infrastructure, configurations, and services
Mobile Application Testing
Comprehensive security testing of iOS and Android mobile applications
🎯 Red Team Assessments
Advanced threat simulation exercises that test your organization's detection and response capabilities through realistic attack scenarios.
What are Red Team Assessments?
Our red team assessments go beyond traditional penetration testing by simulating advanced persistent threats and sophisticated attack campaigns. We test your organization's overall security posture, including people, processes, and technology.
Key Benefits
- Real-world advanced persistent threat simulation
- Assessment of detection and response capabilities
- Testing of security awareness and human factors
- Comprehensive evaluation of security processes
- Improvement of incident response procedures
Red Team Methodology
1. Reconnaissance
Passive and active information gathering about the target organization
2. Initial Access
Gaining entry into target systems through various attack vectors
3. Persistence
Maintaining long-term access to compromised systems
4. Privilege Escalation
Gaining higher-level permissions and administrative access
5. Defense Evasion
Avoiding detection by security controls and monitoring systems
6. Command and Control
Establishing communication channels for ongoing operations
📝 Source Code Analysis
Static code security analysis to identify security vulnerabilities and ensure secure coding practices in your applications.
What is Source Code Analysis?
Our source code analysis services include comprehensive static code review, secure coding consultancy, and implementation of security best practices in your development lifecycle. We examine code before deployment to ensure secure and maintainable applications.
Key Benefits
- Early vulnerability detection in development phase
- Comprehensive code coverage and quality assessment
- Secure coding standards compliance verification
- Reduced security debt and technical debt
- Integration with development workflows and CI/CD
Analysis Coverage
Security Vulnerability Detection
Identification of common security flaws, injection vulnerabilities, and authentication issues
Code Quality Assessment
Evaluation of code maintainability, complexity, and adherence to best practices
Compliance Verification
Ensuring adherence to industry standards like OWASP, SANS, and regulatory requirements
Performance Optimization
Identification of performance bottlenecks and security-related performance issues
🔒 SAST & DAST
Static and Dynamic Application Security Testing solutions to identify vulnerabilities throughout the software development lifecycle.
What are SAST & DAST?
We provide comprehensive application security testing including Static Application Security Testing (SAST) for source code analysis and Dynamic Application Security Testing (DAST) for runtime vulnerability detection. Together, they provide complete security coverage throughout the development lifecycle.
Key Benefits
- Complete white-box and black-box testing coverage
- Runtime vulnerability detection in live applications
- Seamless integration with development lifecycle
- Automated and manual testing approaches
- Comprehensive security validation
SAST Features
- Source code analysis without execution
- Early detection in development phase
- IDE and CI/CD pipeline integration
- Detailed code-level vulnerability insights
- Support for multiple programming languages
DAST Features
- Runtime testing of deployed applications
- Black-box testing approach
- Production environment compatibility
- Real-world attack simulation
- Network and web service testing
🦠 Malware Analysis
Advanced threat analysis and reverse engineering services to understand and mitigate sophisticated malware threats.
What is Malware Analysis?
Our malware analysis services include reverse engineering, behavioral analysis, threat intelligence, and development of custom detection signatures and remediation strategies. We help you understand malware impact and improve your defense capabilities.
Key Benefits
- Deep understanding of threat behavior and capabilities
- Accelerated incident response and containment
- Custom detection signature development
- Enhanced threat intelligence and indicators
- Improved security posture and defense strategies
Analysis Techniques
Static Analysis
Examining malware structure, code, and capabilities without execution in controlled environments
Dynamic Analysis
Running malware in sandboxed environments to observe real-time behavior and impact
Behavioral Analysis
Understanding malware actions, persistence mechanisms, and system modifications
Threat Intelligence
Correlating findings with global threat intelligence and attribution data
Join Our Cybersecurity Team
Be part of a dynamic team protecting organizations from cyber threats
Why Work With Us?
Competitive Compensation
Competitive salary and comprehensive benefits package
Professional Development
Continuous learning opportunities and certification support
Cutting-edge Technology
Access to latest cybersecurity tools and technologies
Collaborative Environment
Work with expert professionals in a supportive team environment
Work-Life Balance
Flexible working arrangements and healthy work-life balance
Remote Options
Hybrid and remote work opportunities available
Apply Now
Submit your application to careers@adastechnologies.org by filling out the form below:
Contact Us
Get in touch with our cybersecurity experts
Get In Touch
info@adastechnologies.org
Phone
+1 (555) 123-4567
Address
123 Security Blvd, Cyber City, CC 12345
Send us your enquiry
Your message will be sent to info@adastechnologies.org